Introduction
In today’s interconnected world, the Internet of Things (IoT) has revolutionized the way we interact with technology. From smart homes to industrial automation, IoT devices have become an integral part of our daily lives. However, with this increased connectivity comes the need for robust security measures to protect sensitive data and ensure safe communication. IoT secure tunneling In this article, we will explore the concept of IoT secure tunneling and its significance in safeguarding IoT ecosystems.
Table of Contents
- Introduction to IoT Secure Tunnelling
- Understanding IoT Communication Channels
- The Importance of Secure Communication
- What Is IoT Secure Tunneling?
- How Does IoT Secure Tunnelling Work?
- Benefits of Implementing IoT Secure Tunneling
- Challenges and Considerations in IoT Secure Tunnelling
- Best Practices for Implementing IoT Secure Tunnelling
- Future Trends in IoT Security
- Conclusion
- FAQ
1. Introduction to IoT Secure Tunneling
As the number of IoT devices continues to grow exponentially, so does the risk of cyber threats and unauthorized access. IoT devices often transmit sensitive data over various communication channels, making them vulnerable to interception and manipulation. IoT secure tunnelling provides a solution to this problem by creating a secure and encrypted pathway for data transmission.

2. Understanding IoT Communication Channels
Before delving into the specifics of IoT secure tunnelling, it is essential to understand the different communication channels used in IoT systems. These channels include wireless protocols like Wi-Fi, Bluetooth, Zigbee, and cellular networks. Each communication channel has its advantages and limitations in terms of range, power consumption, and data transfer rate.
3. The Importance of Secure Communication
Securing IoT communication is crucial to safeguard sensitive data, maintain privacy, and prevent unauthorized access. Inadequate security measures can expose IoT devices to various threats, such as data breaches, device tampering, and denial-of-service attacks. Therefore, ensuring secure communication is vital to the successful deployment and operation of IoT systems.
4. What Is IoT Secure Tunneling?
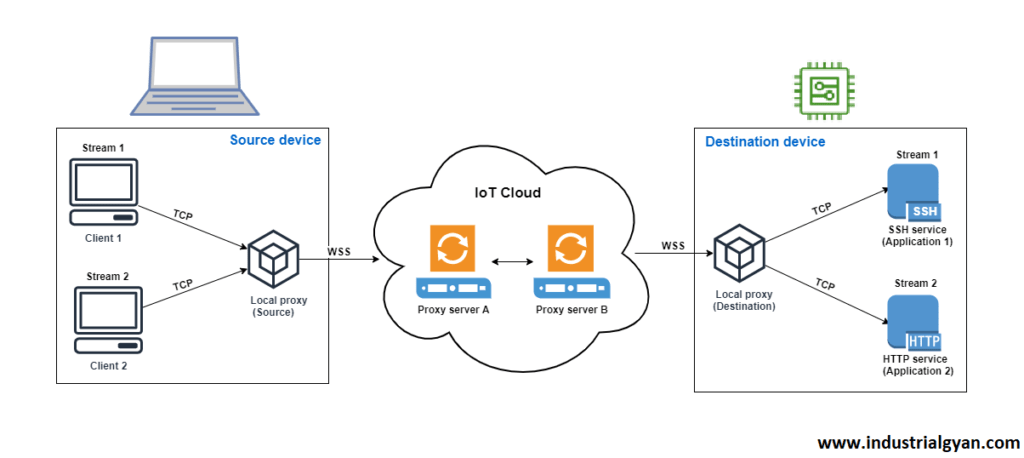
IoT secure tunneling is a technique that establishes a secure communication pathway between IoT devices and the backend infrastructure. It involves encapsulating IoT data within a secure tunnel, which protects it from unauthorized access or manipulation. This tunnel acts as a shield, safeguarding data from potential threats and providing end-to-end encryption.
5. How Does IoT Secure Tunneling Work?
IoT secure tunnelling utilizes various security protocols and encryption algorithms to establish a secure connection. One commonly used protocol is the Transport Layer Security (TLS), which ensures data integrity and confidentiality. Through TLS, IoT devices can authenticate and establish a secure connection with the backend servers, creating a protected tunnel for data transmission.
6. Benefits of Implementing IoT Secure Tunnelling
Implementing IoT secure tunnelling offers several benefits for IoT ecosystems:
- Enhanced Data Security: Secure tunneling protects sensitive data from interception and manipulation, ensuring its integrity and confidentiality.
- Authentication and Authorization: IoT secure tunneling enables device authentication and authorization, preventing unauthorized access to the IoT network.
- Secure Remote Access: It allows secure remote access to IoT devices, facilitating device management and maintenance.
- Compliance with Regulatory Standards: By implementing robust security measures, organizations can ensure compliance with data protection and privacy regulations.
- Trust and Consumer Confidence: Secure communication builds trust among users and fosters consumer confidence in IoT technologies.
7. Challenges and Considerations in IoT Secure Tunneling
While IoT secure tunnelling offers significant advantages, it also presents challenges and considerations that need to be addressed:
- Performance Overhead: Implementing encryption and decryption processes may introduce latency and impact device performance.
- Scalability: As the number of IoT devices increases, ensuring scalable and efficient secure tunneling becomes more complex.
- Key Management: Proper key management is essential to maintain the security of the tunnel and prevent unauthorized access.
- Interoperability: Ensuring interoperability between different IoT devices and platforms can be a challenge in implementing secure tunneling.

8. Best Practices for Implementing IoT Secure Tunnelling
To effectively implement IoT secure tunneling, consider the following best practices:
- Use Strong Encryption: Utilize industry-standard encryption algorithms to ensure robust security.
- Regularly Update Security Measures: Stay updated with the latest security patches and firmware updates to address emerging vulnerabilities.
- Implement Multi-Factor Authentication: Combine different authentication factors to strengthen device security.
- Employ Secure Protocols: Utilize secure protocols like TLS for establishing encrypted connections.
- Conduct Regular Security Audits: Perform periodic security audits to identify and address potential security gaps.
9. Future Trends in IoT Security
The field of IoT security is continually evolving to keep up with emerging threats and technologies. Some future trends to watch out for in IoT security include:
- Artificial Intelligence (AI) for Threat Detection: AI-powered solutions can detect anomalies and potential threats in real-time, enhancing IoT security.
- Blockchain for Data Integrity: Blockchain technology can provide an immutable and tamper-proof record of IoT data, ensuring data integrity.
- Edge Computing for Enhanced Security: By processing data at the edge of the network, IoT devices can reduce latency and improve security by minimizing data exposure.

10. Conclusion
IoT secure tunnelling plays a crucial role in ensuring the security and privacy of IoT ecosystems. By implementing robust security measures and utilizing encryption protocols, organizations can protect sensitive data and mitigate the risks associated with IoT communication. As the IoT landscape continues to expand, the need for secure tunneling will only become more vital in safeguarding our digital future.
11. FAQ
Q1: Can IoT secure tunneling be applied to all types of IoT devices?
Yes, IoT secure tunneling can be applied to various types of IoT devices regardless of their functionalities or industry verticals. It provides a fundamental security layer for data transmission and protection.
Q2: Does implementing IoT secure tunnelling impact device performance?
While there may be a slight performance overhead due to encryption and decryption processes, modern IoT devices and networks are designed to handle the computational requirements without significant impact on performance.
Q3: How can I ensure the interoperability of IoT devices when implementing secure tunneling?
When implementing IoT secure tunneling, it is essential to consider standardized protocols and frameworks that promote interoperability. Adhering to industry standards helps ensure seamless communication between different IoT devices and platforms.
Q4: Are there any specific regulations governing IoT security?
Various regulations and standards govern IoT security, depending on the geographical location and industry. Some notable examples include the General Data Protection Regulation (GDPR) in the European Union and the National Institute of Standards and Technology (NIST) guidelines in the United States.
Q5: How can I get started with implementing IoT secure tunnelling?
To get started with implementing IoT secure tunnelling, it is recommended to consult with security experts and follow industry best practices. Additionally, organizations can leverage secure IoT platforms and solutions that provide built-in security features.
Conclusion
In conclusion, IoT secure tunneling is a crucial aspect of IoT security that ensures safe and encrypted communication between devices and backend infrastructure. By implementing robust security measures, organizations can protect sensitive.
You can follow us on LinkedIn
You can read the article given below:-

I am a highly motivated and skilled individual with a passion for Electrical engineering. I have 1 year of experience in Robotics and Electrical engineering, which has allowed me to develop a strong set of skills in PLC, Painting Robots, SCADA. I am a quick learner and am always looking for new challenges and opportunities to expand my knowledge and skills. I am a team player and enjoy working with others to achieve a common goal. Successfully completed many projects for a various clients in the automobile sector.
Thank You